_readme.txt
ATTENTION!Don't worry, you can return all your files!All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.The only method of recovering files is to purchase decrypt tool and unique key for you.This software will decrypt all your encrypted files.What guarantees you have?You can send one of your encrypted file from your PC and we decrypt it for free.But we can decrypt only 1 file for free. File must not contain valuable information.You can get and look video overview decrypt tool:Price of private key and decrypt software is $980.Discount 50% available if you contact us first 72 hours, that's price for you is $490.Please note that you'll never restore your data without payment.Check your e-mail "Spam" or "Junk" folder if you don't get answer more than 6 hours.To get this software you need write on our e-mail:helprestore@firemail.ccReserve e-mail address to contact us:datarestore@iran.irYour personal ID:0194Asd374y5iuhldmjQby8HJfDgVqVAfkURTeXwrzQ5ym9SJknsR5n6p
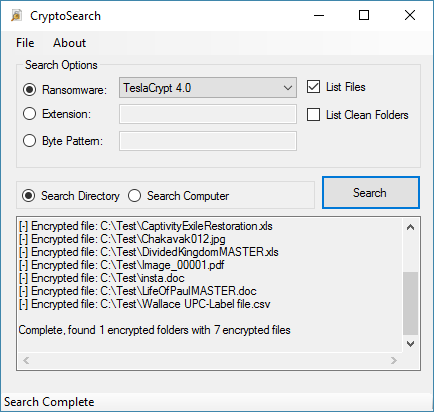
You are infected with STOP (DJVU) Ransomware.This is a support topic specifically for CryptoSearch...it is not intended for questions or assistance about ransomware which has already been identified and for which there is an existing support topic where you can post for help.
Please read the first page of the STOP Ransomware (.STOP, .Puma, .Djvu, .Promo, .Drume) Support Topic for a summary of this infection, it's variants and possible decryption solutions with instructions (including what to do if the decrypter does not work). You need to post any questions or the required information (i.e. Personal ID, Extension of files & MAC (physical) Address of the infected computer) in the above support topic if STOPDecrypter is unable to decrypt your files.
Do not keep posting in the same thing in topics not related to STOP Ransomware.







 Back to top
Back to top